The security of both your data and your customer data is of the utmost importance. According to Germany’s Federal Office for Information Security, more than 6,000 Magento stores were hacked from 2015-2016. So today, I wanted to share my personal 25 Ultimate Security Checks and Habits with you, when setting up a new Magento store.
I can almost guarantee that most of those instances would not have been possible if they had followed this simple list. This is why I wanted to share with you my Magento 2 Security Checklist. Taking note of each of these points will definitely stack the cards in your favour when it comes to Magento security. Some might seem obvious to you, but you may also find some hidden gems.
You may also think that some of these checks are redundant (why do I have to do this, if I’ve already done that), but think of them as fail-safes in case one of these checks fails to stop an attacker in their tracks.
You can download and print this as a checklist for your records here .
1. Backup your store
The first thing you’ll want to consider when running a Magento store is to create external backups of your website and server. Ideally, you’ll want to create 3 types of backups on a regular basis, and the following method always worked for me.
- Once a day, I like to perform an automated backup of my database. After all, this is where all of your settings and data is saved. So it’s very important to back this up regularly.
- At the same time, I also like to take a backup of my Magento Files and Product Images.
- Then once a week, I like to create a complete backup of my entire web server (also referred to as an image backup). This ensures that if something catastrophic happens to my web server, I can at least recreate it from a recent backup.
I’ll schedule all of these to happen when website traffic is at it’s lowest, sometime between 1 am and 4 am. This will obviously vary if your website gets a lot of international visitors. So it might be worth checking Google Analytics to determine the best time.
2. Use a Firewall
The use of a firewall to protect the backend of your Magento store has its Pros and its Cons. The most dominant Pro is that it only allows devices to load the backend (including the login screen) that have an IP address on the servers’ whitelist. This is great because it completely stops any form of brute force access.
However, there are a few downsides to this method depending on your business setup. Firstly, you have to ensure that the device connecting to your website is whitelisted. If not, you’ll have to refer to your server admin to make the necessary changes in order to access the website.
The second, and more impractical of the two, is that you can’t always be sure that a member of your team will be connecting via a Static IP. So if you’re boss, for example, who wants to check Sales Reports whilst he or she is out on their mobile phone or you have a member of staff working from home, then they won’t be able to access anything until their IP addresses have been whitelisted. The reason this is unpractical is that most devices change IP addresses frequently unless you already have some agreement with your Internet Service Provider.
Like I said, a really great option, if everyone who needs access uses a Static IP address. Otherwise, you’re going to upset your Server Administrator every time a change needs to be made.
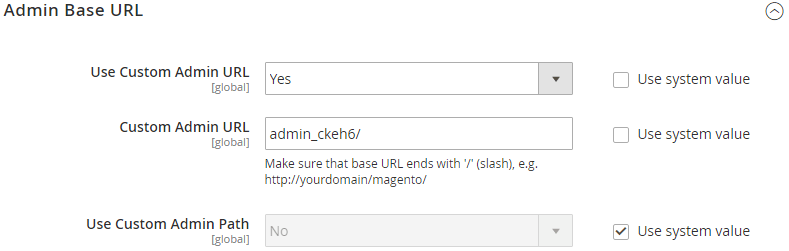
3. Change your Admin URL
A very common mistake to make when setting up your first Magento store is to leave the URL of your backend as /admin . If anyone is looking to gain unauthorised access to the backend of your website, the /admin URL is usually the first to be tested. Instead, use something obscure as it only has to be known by you and your team. Using something like /admin_ckeh6 would be better than just using /admin . Although this isn’t a foolproof method for anyone determined to access your backend login screen, it does help to reduce the exposure to scripts that try to access every Magento website.
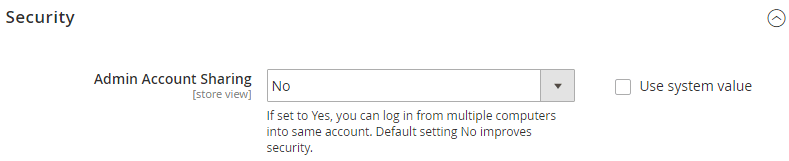
4. Disable multiple computer logins
A really safe way to ensure that another user isn’t using your login credentials is by taking advantage of a new setting that can be found in Magento 2 CE. Under Stores > Configuration > Admin > Security , you will have the option to disable multiple logins from different computers. This means when you come to log in to Magento, it will automatically log anyone out using your current credentials. On the flip side, if you ever get kicked out whilst using Magento, you know that someone has just successfully logged in as you. Now you know you have a problem that needs more investigation.
5. Use SSL on your backend
Not only is it a factor under the Payment Card Industry standard when taking payments on the Frontend of your website, but if you are taking payments on the backend, then you need to be using SSL. SSL encrypts any data that is submitted via your site, thus protecting bother you and your customers. You can enable this under Stores > Configuration > Web .
6. Use strong Admin Passwords
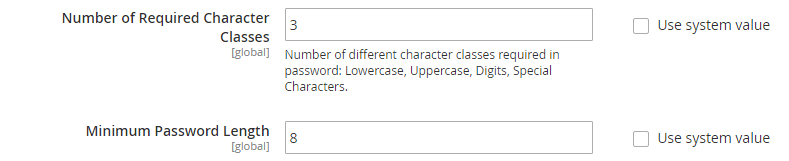
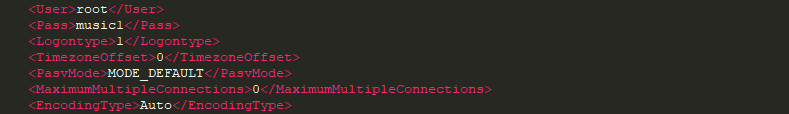
I always assumed it went without saying, that when you create a password for an account, you should use a strong password that can’t easily be guessed. In Magento 1, you had to trust that your team would be sensible when it came down to passwords. No word of a lie, In a previous job, I asked a member of my team to log into his machine so I could check something. He went out and told me that his password was “Music1”!
Anyway, Magento 2 now allows us to force the user to use a password based on whatever strength that you set. This could involve a minimum number of character and numbers, or include special characters or capital letters. The criteria is completely up to you, but whatever you choose here will also affect your customers, so don’t make it too hard for them.
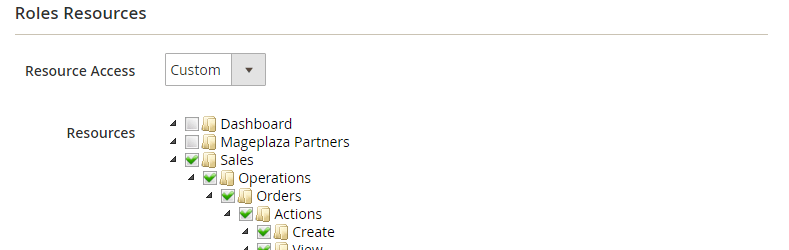
7. Limit Admin Users access
A feature in Magento, that you shouldn’t overlook is the ability to assign user roles. I’m a bit anal when it comes down to this, as I like to perfectly refine what type of user has access to what. To balance too much access vs too little. Setting up user roles such as Management, Sales and Warehouse is a great start when it comes to security and data protection.
Not just that, but limiting access also means that a user can’t accidentally change a setting that they don’t have access to. You certainly wouldn’t want one of your warehouse pickers accidentally deleting a product instead of updating its inventory. Also, if one of your users’ credentials does get leaked, then it will at least limit the damage that can be done.
As a final note, if you are the one who has setup Magento then that means you’ll be using an account with Admin level access. My advice to you is to create yourself a lower tier access account for everyday use and avoid using your Admin account unless you really need it.
8. Don’t share User logins
A classic example of poor practice when it comes to security is by sharing login details with a colleague. Whether your colleague got locked out and needs to log in, or you have a new starter that hasn’t been assigned a login yet, don’t be tempted to share your login details. It’s bad practice for any account, not just Magento.
9. Don’t use obvious login names
Having a username and a password is like having 2 stages of security in one. The attacker has to guess both your username and your password. A couple of common formats of username is a plain name, such as “Bob” or “Smith”, and the other is to include a dot like an email address such as “b.smith” or “bob.s”.
Instead, try and come up with something more creative like their surname and employee number for example “smith022”. Also, make sure you remove any names like Support, Admin or Manager from the user list.
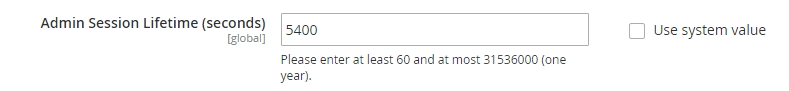
10. Limit Admin session times
Getting kicked out of Magento after a period of time is a pain in the ass. Sometimes I’ve started processing a sale on the backend, only to be caught on the phone for a long time. Then when you come to complete the transaction by pressing ‘Place Order’, you get kicked out because of a timeout, and then have to restart again.
As annoying as this is, it’s no excuse to set an Admin Timeout limit of 24 hours. This feature is in place for your security. I think the default is 20 minutes, so if you do need to increase the time, set it for an hour (which is 3600 seconds).
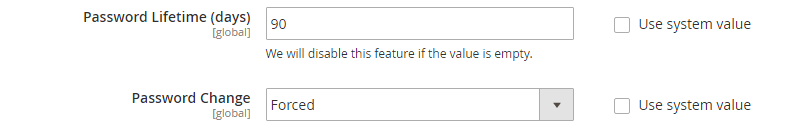
11. Force password updates
Magneto 1 CE didn’t come with this option as it was reserved with their Enterprise Edition. However, in Magento 2 we finally get this feature out of the box, so take advantage of it. If you go to Stores > Configuration > Admin > Security , you will see an option to force a password reset every 90 days. Feel free to lessen this timeframe but definitely turn it on, as many users can become complacent. The longer you use a password, the easier it is for someone to crack.
12. Use case sensitive logins
This was also another option that wasn’t available to us in Magento 1, but is a great feature that we can now use to help fight against anyone trying to brute force their way into Magento backend. Under Stores > Configuration > Admin > Security , you’ll find the option to enable Case Sensitivity. I recommend enabling this to cut down on password guessing.
13. Remove old users
Like any job, staff come and go. And when a member of your team leaves, you can often overlook removing their credentials from your Magento instance. This doesn’t just apply to Magento, this could also apply to your payment gateways or emails. It might be worth keeping a list of websites so you can ensure you check all access to all sites have been removed when you have a member of staff leave your business.
14. Check for new admin users
When someone malicious hacks your website, you won’t always notice. It would actually be quite dumb of that user to hack in and make it obvious by trashing your site. What they will tend to do instead is create themselves an Admin Account so that they can log in and out whenever they chose. It’s a common tactic that you should be aware of.
So try and get into the routine each month in auditing the Admin Users on Magento for anyone who should or shouldn’t be there, whilst taking note of their Access Level. If you do find a user that’s out of place, don’t just delete the account and forget about it, instead, complete a full investigation as they may still have the ability to create another user.
15. Saving passwords
Saving passwords is your browser is awesome because it allows you to use different passwords for different accounts without needing to remember them all. You can save the credentials for almost any website from Pinterest, to PayPal, if you’re logged into something like Google Chrome. So the next time you log in, the fields will conveniently autofill with your username and password. But what I find is often overlooked is the password to your Gmail account that saves all of those passwords.
There’s no point using a 16 alphanumeric password with special characters on all of your accounts if the password to your Gmail account that stores all of those passwords is “music1”. Just saying…
16. Avoid running other software on your server
It’s tempting to save a few quid by running other software on your web server. For instance, you might be running another version of Magento for a different store, or Running a blog using WordPress. The problem is, that if either of those 2 instances gets attacked, it could compromise your entire server, affecting all of your websites in one go. Just keep that in mind if you ever consider running more than one platform on your web server.
17. Don’t save your password in FTP Programs
If you’ve ever used an FTP Program on your computer to transfer files to and from your server, then you’ll have been given the opportunity to save your Username and Password within the program. Take FileZilla for example… When you create a new Bookmark with the program, you can choose whether to save the password. But when you do, it just stores it as plain text on your hard drive. Bare that in mind, especially if you use a shared computer.
18. Look after your machine security
One of the easiest ways to hack into Magento is by using a machine that’s already logged on. So it’s my recommendation that you always run an up-to-date Antivirus and Firewall Software on the computers that you use to access Magento. It’s crazy how many people I know that don’t bother with an Antivirus or Firewall on their computer. If your system has been compromised, then any sort of malicious software could help someone gain access to Magento. For instance, they could key-log or screen share your system to get customer information.
Another important habit to get into is to lock your computer when you leave your desk. When I used to work in a call centre for a mortgage company, anyone caught doing this would be hung if caught. This has always stuck with me and triggers me now if I don’t see others do it. Yes, you may not be working in a bank, but you’re still dealing with customer details and payment information. And if you use Magento as your POS System in a brick and mortar store, don’t let me catch you leave the till unattended!
19. 3rd Party Support
Sometimes, you might need to draft an individual or a company to help fix a problem. The most common occurrence is when you have an extension or theme that does not behave as intended. For example, an extension that you installed has somehow broken the appearance of your product pages after you install it. You asked the developer for assistance, and they ask you for login details to investigate.
Firstly, never give them your own login details. Instead, create them a temporary username and password for them to use on your Development site. Second, never give them complete admin or root level access – Only give them access levels that they require. If they are working on the Development site (which they should be), it can still tell them a lot about your Production site. Finally, as soon as they are finished, remove the username and password that you created for them.
20. Update your Extensions
If your Magneto instance uses 3rd Party Extensions by reputable developers, then there is a high chance they will be supporting this with security updates. You’ll often find that after a Magento update, Extensions will get patched to support the update. The problem is, you don’t always get notified of these Extension Updates, and if you do, it can sometimes be overlooked by a number of promotional emails that developers sometimes send out. You also can’t rely on check the Web Setup Wizard for updates, as your method of installation can sometimes affect whether you see available updates or not.
My advice is to make a habit of checking the websites where you purchased extensions from to see if an update has come out. Then taking action if it has.
On the occasions where you have developed your own extensions, or use an extension that is no longer supported, you or your developer should take the time to revisit your code to make any appropriate changes that may have been triggered by a Magento update.
21. Update your Magento
And that leads me nicely into Magento updates/upgrades. Magento is a big player when it comes to eCommerce Platforms, and that just makes it a bigger target when it comes to people finding exploits. Some people look at finding these exploits as a hobby or a job. And some people report those vulnerabilities to Magento and others take advantage of them for their own gain.
The good guys that find exploits, inform Magento. Then Magento will normally patch the issue and make an announcement about the patch to everyone when they launch it to explain what the issue was. This means that the bad guys now know this vulnerability and can start attacking out-of-date stores with this knowledge. This is why it’s important to update Magento whenever a patch or upgrade is announced.
I wouldn’t suggest dropping everything and deploying the update the moment it comes out, as some patches get hot-fixed within a few days because of unforeseen issues. But always aim to update Magento within a couple of weeks.
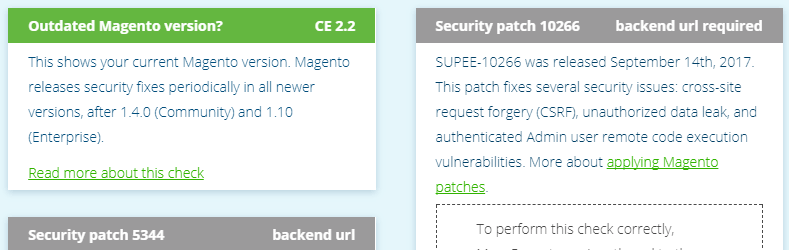
22. Magereport.com
Magereport.com is a free online service recognised for its security checks within the Magento community. It’s super simple to use. Simply visit magereport.com, enter the URL of your Magento 2 store, and within a few seconds, it will check your website for known vulnerabilities.
For each vulnerability, you will either PASS, FAIL or get an UNKNOWN. Green , results in a PASS and Orange results in a FAIL, highlighting that you should be dealing with this immediately. It’s quite common to get UNKNOWN results as certain security measures can interfere with security scans. Just make sure that you investigate these by clicking on the provided links within each result.
You’ll notice on the left that you can subscribe to the report, so if any new vulnerabilities get added to MageReport, you’ll be notified if you are affected. Just remember, anyone can view these reports, so stay on top of this. As great as this tool is, you should only use as a guide as some custom configurations can lead to false positives or negatives.
23. Magento Security Scan
Another very recent service that came out, just days ago, is Magento’s very own Security Scan Tool. Just like Magereport, this free online tool allows you to monitor your Magento store and send you email alerts if it detects any known security risks, malware and unauthorised access. Even though this new security tool is very similar to Magereport, it can’t hurt to use both tools.
You can access the security tool by logging into your Magento.com account. From there, you will see a link to the Security Tool scan where you can add the URL of your store and schedule scans.
24. Choose a reputable Web Hosting Service
Choosing a company to host your Magento store can be quite a drawn-out and complicated task if you’ve never done it before. Balancing between Cost, Features and Support. I would highly recommend doing your research and selecting a reputable company, and not be drawn into the cheapest hosting options. The best types of Hosting for the inexperienced are Managed Solutions. You’ll normally find that they’ll look after your Web Server by applying security updates to the Operating System whenever necessary, and can support you when you need it most.
If you’re totally stuck on choosing a Magento Web Host, I personally use Nexcess.net.
25. Create a disaster recovery plan
Let’s assume for a moment that the worst has happened to your Magento store and your website has been compromised. What do you do? Who do you contact? What does your team do whilst your website is offline? Do you close the phone lines or have your team continue to answer them? These are the kind of questions that you really need to sit down and think about.
Luckily, if you followed the very first point in the checklist, then you’ve been making regular backups. You need to think about how to access those backups and how to use them to get your website up and running again. There are many factors to think about, and it may be a document that you work on over a long period of time. But make sure that document is accessible to those who might need it in case of an emergency.
You can use this link to a Disaster Recovery Plan Template I found here.
Summary
I could have gone deeper into this checklist by including the web server, but frankly, that’s way outside the scope of this video and you should really speak to your Server Hosting Company or System Administrator about it. Anyway, I hope that you found this security checklist useful because it’s a great starting point when setting up a new Magento store. If I missed any, then please share with me in the comments below.